Learn about the benefits of implementing the NIST Cybersecurity Framework 2.0 and its role in enhancing cybersecurity measures for businesses of all sizes and industries.
Introduction to the Framework
The NIST Cybersecurity Framework (CSF) 2.0 helps businesses enhance their cybersecurity posture by providing a systematic approach to managing cybersecurity risks. This Framework, developed by the National Institute of Standards and Technology (NIST), has a rich history of contributing to the establishment of robust cybersecurity standards. By aligning themselves with CSF 2.0, businesses can improve their overall cybersecurity resilience.
NIST plays a pivotal role in shaping cybersecurity standards by working closely with industry experts and stakeholders to develop comprehensive guidelines. This collaboration ensures that cybersecurity measures are aligned with the latest technologies and emerging threats, significantly influencing global cybersecurity practices. By leveraging the collective expertise of professionals in the field, NIST provides organizations with the necessary tools to safeguard their digital assets and operations.
The CSF 2.0 offeres organizations a structured framework to better protect their digital assets and critical information. By understanding and implementing the CSF 2.0, businesses can proactively implement measures to secure their systems and data.
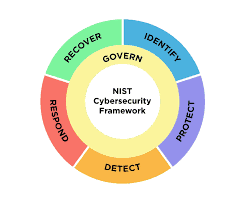
Let’s Get Started: The Core of CSF 2.0
The CSF 2.0 is a comprehensive tool that offers organizations a structured approach to effectively managing cybersecurity risks. Most importantly, the Core functions within the framework provide organizations with a clear roadmap for enhancing their cybersecurity posture.
Here’s a quick breakdown of the CSF 2.0 Core functions and what they mean:
Identify
Understand what digital assets you need to protect (data, systems, software).
Protect
Put safeguards in place to reduce the chances of a successful cyberattack.
Detect
Implement technologies and processes to spot potential cybersecurity incidents quickly.
Respond
Have a plan to contain threats, limit damage, and communicate effectively.
Recover
Be able to restore normal operations and systems after an incident.
Govern
Establish clear cybersecurity roles, responsibilities, policies, and procedures within your organization.
That last function, Govern, is new to the updated CSF and is highly significant. By including the new “Govern” function, the framework provides a structured approach for organizations to establish robust cybersecurity governance programs and activities, thereby enhancing their overall cybersecurity maturity. This shift towards governance signifies a strategic move towards elevating risk management to an enterprise level, underlining the necessity for key leadership involvement and continuous governance throughout security management processes.
Moreover, the framework’s alignment with Zero Trust principles signifies a paradigm shift towards more secure digital practices. Zero Trust principles advocate for continuous verification and strict access controls to mitigate the risk of cyber breaches. By integrating these principles, the CSF 2.0 aims to instill a culture of heightened security awareness and proactive measures within organizations, fostering a cybersecurity posture that is resilient and adaptive to modern threats. This alignment with contemporary security philosophies ensures that the framework remains relevant and effective in combating evolving cybersecurity challenges.
Another significant change to the revised CSF 2.0 is its increased flexibility, enabling organizations to adapt the framework to their specific needs and environments. The framework now provides a more tailored and scalable approach to cybersecurity, allowing businesses to align their practices with industry standards. This flexibility not only enables organizations to address their unique cybersecurity challenges but also promotes a proactive stance in managing potential risks and vulnerabilities.
The CSF 2.0 also emphasizes the importance of continuous improvement, integration of privacy considerations, and resilience in cybersecurity practices. For instance, organizations can utilize the framework to evolve their security postures continuously, adapting to the ever-changing threat landscape and emerging vulnerabilities. Additionally, the framework’s focus on resilience underscores the significance of building robust security measures that can withstand and recover from cyber incidents effectively, enhancing overall cyber resilience within organizations.
Why Should I Care About Governance?
Cybersecurity governance is the foundation upon which organizations build their security strategies. Its inclusion in the Core of CSF 2.0 emphasizes its tremendous importance. Governance involves the development and implementation of policies, procedures, and controls to ensure that cybersecurity measures align with business objectives and regulatory requirements. A cybersecurity governance framework should include regular security assessments, risk management protocols, incident response plans, and more–these actions can help organizations effectively mitigate cyber risks and respond promptly to incidents when they do occur.
The /ctrl-center/back-office-stuff-no-more-how-cybersecurity-governance-can-supercharge-your-business/ not only focuses on preventing cyber threats but also on promoting a culture of security awareness throughout the organization. By fostering a security-conscious environment, businesses can empower employees to identify and report potential security incidents, participate in cybersecurity training programs, and adhere to best practices for data protection. This proactive approach to cybersecurity governance strengthens the organization’s overall security posture and minimizes the likelihood of successful cyberattacks or data breaches.
Benefits of Adopting the Framework
Adopting the CSF 2.0 can yield numerous advantages for businesses. One key benefit is the framework’s alignment with the National Cybersecurity Strategy, which ensures that organizations can adhere to the latest cybersecurity standards and practices endorsed at a national level. For instance, by incorporating the framework’s guidelines into their cybersecurity protocols, organizations can demonstrate a commitment to upholding industry best practices and safeguarding their digital assets effectively.
Moreover, the expanded scope of the CSF 2.0 beyond critical infrastructure will assist businesses across various sectors to fortify their cybersecurity defenses. For example, companies in the financial services industry can utilize the framework to enhance data protection measures and mitigate the risks associated with cyber threats, ultimately safeguarding sensitive financial information from unauthorized access. Additionally, the inclusion of quick-start guides tailored for different user types within the framework empowers organizations to navigate its implementation seamlessly and derive maximum value from the recommendations.
All that being said, it’s important to understand that the potential benefits of adopting the CSF 2.0 extend beyond regulatory alignment and incident reduction. Companies that have embraced the framework have reported increased operational efficiency and a more comprehensive understanding of their cybersecurity landscape. This deeper insight allows organizations to proactively identify and address vulnerabilities, ultimately bolstering their cybersecurity defenses and safeguarding critical assets from potential threats. By leveraging the scalability of the CSF 2.0, businesses of all sizes and industries can tailor the framework to suit their specific cybersecurity needs, ensuring a customized and effective approach to managing cybersecurity risks.
Implementation: Best Practices
Developing a specific plan tailored to the organization’s needs is crucial for successful implementation. Monitoring progress throughout the implementation process is equally vital, allowing organizations to identify challenges, make necessary adjustments, and track the effectiveness of their cybersecurity initiatives. By regularly reviewing and assessing the implementation progress, organizations can ensure that they are on track to achieve their cybersecurity objectives and enhance their overall security posture.
When implementing the CSF 2.0, organizations should prioritize gaining a detailed understanding of the specific pillars outlined in the document.
- The Policy pillar involves establishing clear and robust cybersecurity policies that align with the organization’s goals and compliance requirements.
- By defining comprehensive Procedures, companies can ensure that their cybersecurity practices are consistently followed and that all employees understand their roles and responsibilities in maintaining security.
- The Roles and Responsibilities pillar emphasizes assigning cybersecurity duties to individuals or teams within the organization, ensuring accountability and effective execution of cybersecurity measures.
- The Culture pillar underscores the importance of fostering a cybersecurity-aware culture throughout the organization, encouraging employees to prioritize security in their daily operations. The
- The Metrics and Measurement pillar stresses the significance of quantifying cybersecurity efforts, enabling organizations to track progress, identify gaps, and continuously improve their security posture.
By focusing on these specific pillars, organizations can ensure a comprehensive and structured approach to cybersecurity in line with the framework’s guidelines.
Using the Reference Tool, another newcomer in the NIST CSF 2.0, can significantly benefit organizations seeking to align their practices with the framework’s recommendations. This tool provides a structured approach for customizing cybersecurity strategies based on an organization’s unique requirements and risk profile. The Reference Tool helps businesses identify specific areas where improvements are needed, prioritize cybersecurity initiatives, and establish a roadmap for enhancing their security posture. Moreover, aligning cybersecurity strategies with the guidelines provided in the Reference Tool enables organizations to effectively address current and emerging cybersecurity challenges, ultimately strengthening their overall resilience to cyber threats.
Last but absolutely not least, gaining buy-in from stakeholders at all levels of the organization is essential. Executives, IT teams, and employees alike should understand the importance of the framework and actively support its implementation. From leadership to operational staff, each stakeholder’s understanding and commitment is essential for the successful adoption of the framework.
Implementation: Common Challenges
Implementing the NST Cybersecurity Framework 2.0 presents several common challenges that organizations need to address. One significant challenge is the resource-intensive nature of the implementation process, requiring substantial financial investments, time commitments, and skilled personnel. For example, organizations may need to allocate dedicated cybersecurity teams or hire external experts to ensure the successful adoption of the framework, which can strain resources and budgets.
Moreover, customizing the framework to align with the specific needs and requirements of individual organizations can lead to complexity and potential roadblocks in implementation. For instance, organizations operating in highly regulated industries may need to navigate intricate compliance frameworks while integrating the CSF 2.0, adding layers of complexity to the implementation process. This customization process demands detailed assessments of existing cybersecurity practices, thorough gap analyses, and tailored action plans to bridge identified gaps effectively.
Furthermore, there’s a natural resistance to change within most organizations, and this sense of inertia can impede the seamless integration of the framework. Employees accustomed to existing protocols may resist adopting new procedures or technologies outlined in the CSF 2.0. Overcoming these challenges requires strong leadership support, effective change management strategies, comprehensive training programs, and clear communication to ensure buy-in at all levels. Remember: Cybersecurity is an ongoing process, not a one-time fix. The CSF 2.0 is really just the start of your journey towards improved security.
Getting Help: The TMG Advantage
Engaging with security service providers such as TMG can significantly benefit organizations in their journey to implement the CSF 2.0. We offer specialized knowledge and guidance that can help you navigate the intricacies of aligning with the framework’s requirements.
We can also help organizations identify and protect their valuable assets from cyber threats while implementing robust access control measures to enhance overall data security. By partnering with service providers, organizations can proactively address cybersecurity challenges, improve incident detection capabilities, and develop comprehensive response and recovery plans to mitigate potential cyber risks.
At TMG, we’re passionate about helping businesses strengthen their cybersecurity defenses. We understand the NIST CSF 2.0 framework inside and out, and we can help you customize it to fit your business perfectly. Want to learn how TMG can transform your cybersecurity approach? Contact us today.

0 Comments